From ISO to DORA: Who Wants You to Hack Yourself—and How Often
Pen tests and red teaming aren’t just best practices—they’re regulatory requirements. This guide breaks down ISO, PCI DSS, DORA, NIS2, and more in one clear table so you know exactly what’s mandatory.

Introduction
In today’s dense and fragmented cybersecurity landscape, organizations—especially those operating in regulated sectors—are expected to proactively test and secure their systems against a barrage of threats. At the heart of this defense lie three technical pillars: penetration testing, red teaming, and vulnerability management. These aren’t just buzzwords—they are specific, high-stakes practices meant to expose and fix weaknesses before attackers find them.
Yet as crucial as these activities are, the rules surrounding them are a maze. Standards like ISO/IEC 27001 emphasize risk-based testing without mandating specific actions. Others, such as PCI DSS, EU NIS2, and DORA, impose prescriptive and often overlapping requirements. Sector-specific frameworks like TIBER-EU and SWIFT CSCF add another layer, turning security compliance into a complex game of interpretive cartography.
This research cuts through that complexity. The aim is to bring clarity by identifying and comparing what each major standard and regulation actually requires when it comes to these three core practices. It’s not about theory—it’s about what you must do, what you should do, and what regulators expect you to prove.
Structure of the Article
First, you'll find a side-by-side comparison TL:DR table summarizing the penetration testing, red teaming, and vulnerability management requirements across six major standards and regulatory frameworks. It’s built for a 5-minute read so you can get the essentials at a glance.
Following the table is a deeper dive into each standard, including its scope, specific obligations, nuances around testing frequency, and links to authoritative source material. This section provides the interpretive muscle behind the table and gives context for planning compliance or improving cyber defense posture.
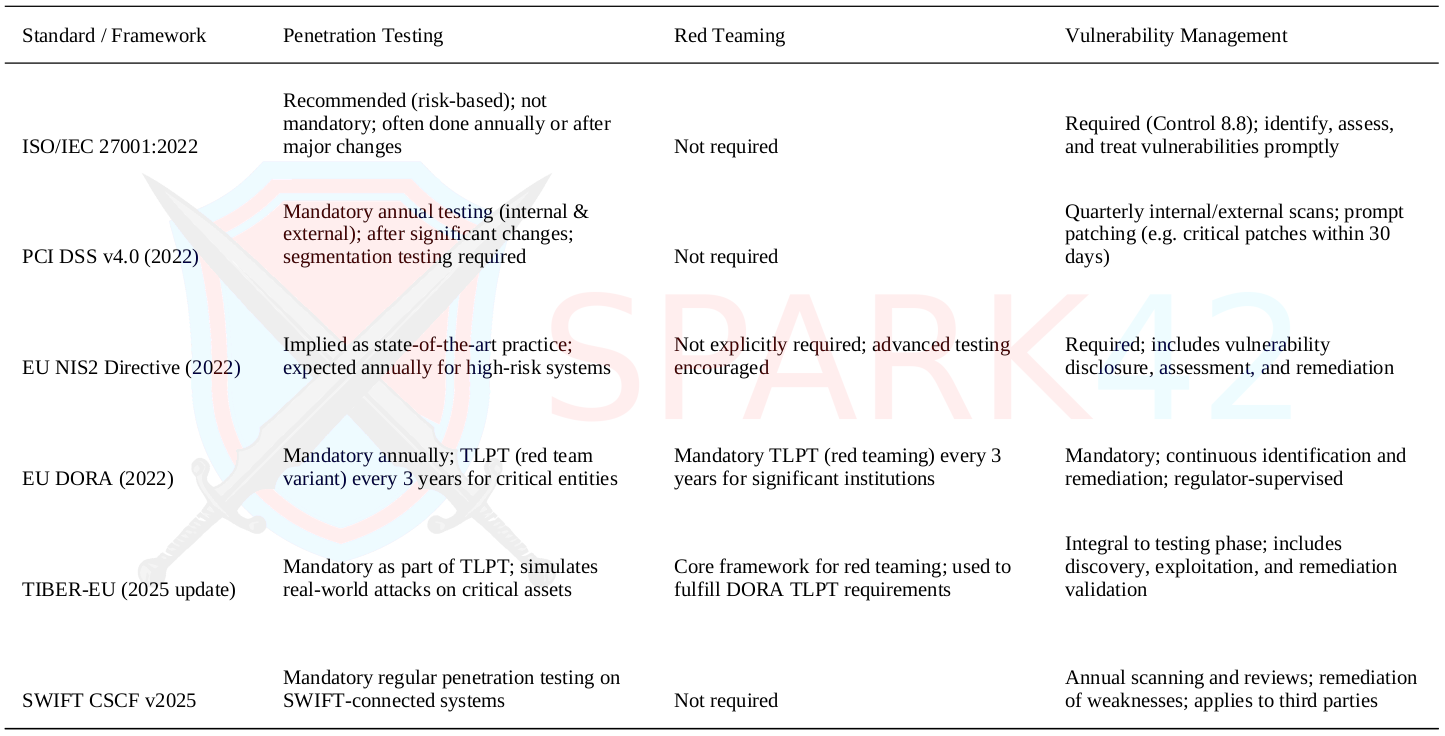
Side-by-Side Comparison of Security Testing Requirements Across Standards
This TL:DR table summarizes how major cybersecurity standards and regulations—ISO 27001, PCI DSS, NIS2, DORA, TIBER-EU, and SWIFT CSCF—approach penetration testing, red teaming, and vulnerability management.
Deep Dive: How Key Standards Handle Security Testing and Vulnerability Management
After the high-level comparison, it’s time to roll up our sleeves. In this section, we explore how each major cybersecurity standard or regulation addresses penetration testing, red teaming, and vulnerability management—one by one. From broad international standards like ISO/IEC 27001 to highly targeted mandates like DORA and SWIFT CSCF, each framework carries different expectations for how often and how deeply organizations should assess their defenses.
You’ll find the nuances that don’t fit in a summary table: how strongly tests are emphasized, which controls imply continuous scanning, and whether red teaming is advisory or legally binding. Each standard is presented with its latest release context and a focus on actionable security obligations. Links to original sources are included where available, so you can dig deeper or validate interpretations directly.
ISO/IEC 27001 (ISO 27k Series)
Release: October 2022.
Scope: International standard for Information Security Management Systems.
Pen Testing & Vulnerability Management: ISO 27001:2022 emphasizes a risk-based approach to security. It includes a control for managing technical vulnerabilities (Annex A 8.8) which requires identifying, assessing, and promptly addressing security weaknesses. While ISO 27001 does not explicitly mandate regular penetration tests, in practice organizations are expected to perform periodic security testing as part of good risk management [riskcrew.com, riskcrew.com]. Auditors and best practices typically call for ongoing vulnerability scanning (e.g. quarterly) and penetration testing at least annually or after significant changes to demonstrate ISO 27001 compliance [riskcrew.com]. The 2022 update also added new controls (e.g. on secure development and testing) that reinforce the value of regular security testing in the ISMS. In summary, ISO 27001 requires a documented vulnerability management process and encourages regular security assessments (including pen tests) to ensure controls are effective, though specific frequencies are determined by risk [riskcrew.com].
PCI DSS v4.0 – Payment Card Industry Standard
Release: March 2022 (PCI DSS version 4.0).
Scope: Industry standard for organizations handling payment card data (global, including EU).
Pen Testing & Vulnerability Management Requirements: PCI DSS prescribes detailed technical security controls, including explicit requirements for penetration testing and vulnerability scanning:
- Quarterly Vulnerability Scans: Perform internal and external network vulnerability scans at least quarterly and after any significant changes. (External scans must be by an approved vendor, and PCI DSS 4.0 adds that internal scans should be authenticated for deeper coverage [blazeinfosec.com].)
- Annual Penetration Tests: Conduct penetration testing on the cardholder data environment (both external-facing and internal systems) at least annually, and after any significant infrastructure or application changes [blazeinfosec.com]. These tests must follow industry-standard methodologies and include verifying that segmentation controls (if used to isolate card data) are effective [blazeinfosec.com].
- Prompt Remediation: Identify and remediate high-risk vulnerabilities. (PCI DSS also requires a process to install critical security patches within one month of release as part of vulnerability managementblazeinfosec.com.)
In essence, PCI DSS obligates organizations to continuously manage vulnerabilities (through scanning and patching) and to regularly test their security via penetration tests to protect cardholder data [blazeinfosec.com, blazeinfosec.com].
EU NIS2 Directive – Cybersecurity for Essential Sectors
Release: November 2022 (Directive (EU) 2022/2555), to be transposed into national laws by 2024–2025.
Scope: EU-wide cybersecurity requirements for “essential” and “important” entities (energy, health, finance, transport, digital infrastructure, etc.).
Pen Testing & Vulnerability Management: NIS2 requires organizations to implement a broad set of cyber risk management measures, including vulnerability handling and regular security assessments. While not prescriptive on exact techniques, the directive stresses “state of the art” protections and the quick detection and remediation of exploitable vulnerabilities [sits.com]. In practice this means having policies for technical vulnerability management and disclosure, and periodically evaluating the effectiveness of security controls (e.g. through tests and audits). EU guidance under NIS2 highlights that regular penetration testing is a key tool to identify missing patches or weak credentials and to verify that security measures work [sits.com]. In fact, NIS2’s recitals explicitly mention penetration tests as a way to find unaddressed updates or misconfigurations [sits.com]. Many organizations under NIS2 are therefore expected to conduct independent penetration tests at least annually (especially for high-risk systems) as part of their compliance, with tests ideally performed by qualified external experts [sits.com]. In summary, NIS2 pushes companies to maintain robust vulnerability management processes and to use regular security testing (including pen tests) to achieve appropriate cybersecurity hygiene [sits.com, sits.com].
EU Digital Operational Resilience Act (DORA) – Financial Sector
Release: December 2022 (Regulation (EU) 2022/2554); applicable from Jan 2025.
Scope: EU regulation for financial entities (banks, insurers, investment firms, payment providers, etc.) to ensure operational resilience, including cyber resilience.
Pen Testing & Vulnerability Management: DORA introduces strict testing obligations for financial institutions’ ICT systems:
- Annual Testing Program: All in-scope financial entities must conduct regular digital operational resilience testing (DORT) of their systems each year [yogosha.com]. This includes vulnerability assessments, security audits, penetration testings etc., to proactively uncover weaknesses. However, the phrasing “shall provide for” and “appropriate tests, such as” allows flexibility in how often specific tests are performed, provided critical systems are adequately tested each year [digital-operational-resilience-act.com, digital-operational-resilience-act.com].
- Threat-Led Penetration Testing (TLPT): For the most significant (critical) institutions, DORA requires a specialized intelligence-led red team exercise at least once every 3 years [yogosha.com]. These TLPTs are advanced penetration tests that mimic tactics, techniques, and procedures of real threat actors in a controlled attack on the organization’s live production systems [yogosha.com]. The scope must cover critical functions and be approved by regulators, and the tests must be performed by independent, highly qualified testers under strict conditions [digital-operational-resilience-act.com, yogosha.com]. After each TLPT, a report of findings and remediation plans must be submitted to the regulator [yogosha.com].
DORA effectively mandates a tiered approach: continuous vulnerability management and yearly security testing for all firms, and rigorous red team-style testing for major institutions. The TLPT requirement formalizes red teaming as a compliance activity – firms must use certified or accredited testers and threat intelligence to simulate real-world attacks, and regulators oversee the process [digital-operational-resilience-act.com, yogosha.com]. Notably, the European Supervisory Authorities are developing technical standards for TLPT, and the European Central Bank’s TIBER-EU framework has been updated (in 2025) to align with DORA’s red teaming requirements [ecb.europa.eu]. Overall, DORA places strong emphasis on robust vulnerability remediation and regular, realistic testing of cyber defenses to ensure financial systems’ resilience.
Threat Intelligence–Led Red Teaming Frameworks (TIBER-EU & CBEST)
In the financial sector, regulators have promoted dedicated red team testing frameworks to complement the above standards. CBEST (launched in the UK in 2014) was one of the first such schemes, introducing controlled threat intelligence-led penetration tests for major banks [nortonrosefulbright.com]. It uses intelligence from government and private sources to emulate advanced attackers targeting critical assets, and has since influenced other countries. Building on similar principles, the European Central Bank introduced TIBER-EU (Threat Intelligence-Based Ethical Red Teaming) in 2018 as a common framework for EU member states. TIBER-EU provides detailed guidance on conducting red team exercises – from scoping and threat intel to test execution and remediation – in a safe and uniform way. In February 2025, the Eurosystem updated the TIBER-EU framework to align with DORA’s TLPT requirements, incorporating DORA’s standards into TIBER’s process and making “purple teaming” (collaborative red/blue) a mandatory aspect [ecb.europa.eu, ecb.europa.eu]. These frameworks are not laws themselves, but they are often adopted by regulators and firms to meet regulatory expectations. Under DORA, for example, a TIBER-EU style approach can be used to satisfy the mandated red team tests [ecb.europa.eu]. In summary, CBEST, TIBER-EU and similar frameworks (e.g. TIBER-NL in Netherlands, iCAST in Asia) set out how to conduct intelligence-driven red team exercises that simulate realistic attacks on critical systems, providing a standardized way to test and bolster cyber resilience in regulated industries.
SWIFT Customer Security Controls Framework (CSCF) – 2025 Updates
Release: 2024–2025 (latest version v2025).
Scope: Security standard for banks using the SWIFT interbank network (global financial industry).
Pen Testing & Vulnerability Management: The SWIFT CSCF is an industry-driven compliance framework that includes mandatory controls for technical security. In recent versions, SWIFT has tightened requirements for testing security measures. Notably, Control 5.2 requires regular penetration testing of the SWIFT environment – penetration tests are now a mandatory part of the annual SWIFT compliance audit, aimed at verifying the resilience of systems against attacks [infoguard.ch]. Banks must conduct and document these tests routinely, and address any findings as part of their security strategy. Likewise, Control 5.1 mandates vulnerability scanning and security reviews at least annually, including assessment of critical systems and relevant third-party providers [infoguard.ch]. Together, these controls ensure SWIFT members are proactively identifying vulnerabilities and testing their defenses. The 2025 update stresses that institutions should “test, document, and adapt” all cybersecurity controls continuously – not just via selective checks, but as an integral, ongoing process [infoguard.ch]. In summary, to remain SWIFT-compliant, financial institutions must implement a strong vulnerability management program (with regular scans) and perform frequent penetration tests on their SWIFT-related infrastructure, providing evidence of remediation and cyber resilience [infoguard.ch, infoguard.ch].
Final remarks
Each of the above standards and regulations – from the general ISO/IEC 27001 and PCI DSS, to EU laws like NIS2 and DORA, and down to sector-specific frameworks – underscores the importance of regular vulnerability management and security testing. Organizations in regulated and security-conscious industries are expected to continuously scan for weaknesses, promptly patch or mitigate vulnerabilities, and periodically probe their own defenses through penetration tests or full-scale red team exercises. These practices are not only critical for compliance but are recognized as best-practice measures to manage cyber risk and improve an organization’s security posture [sits.comsits.com].